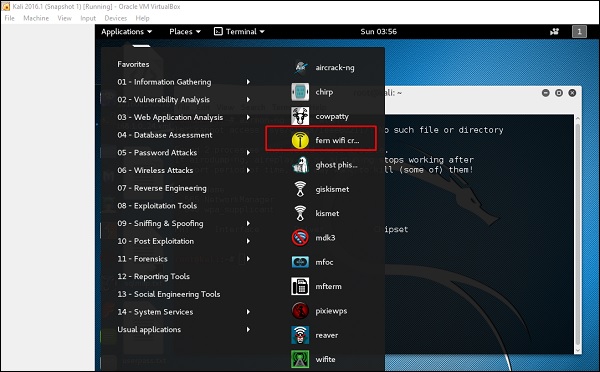
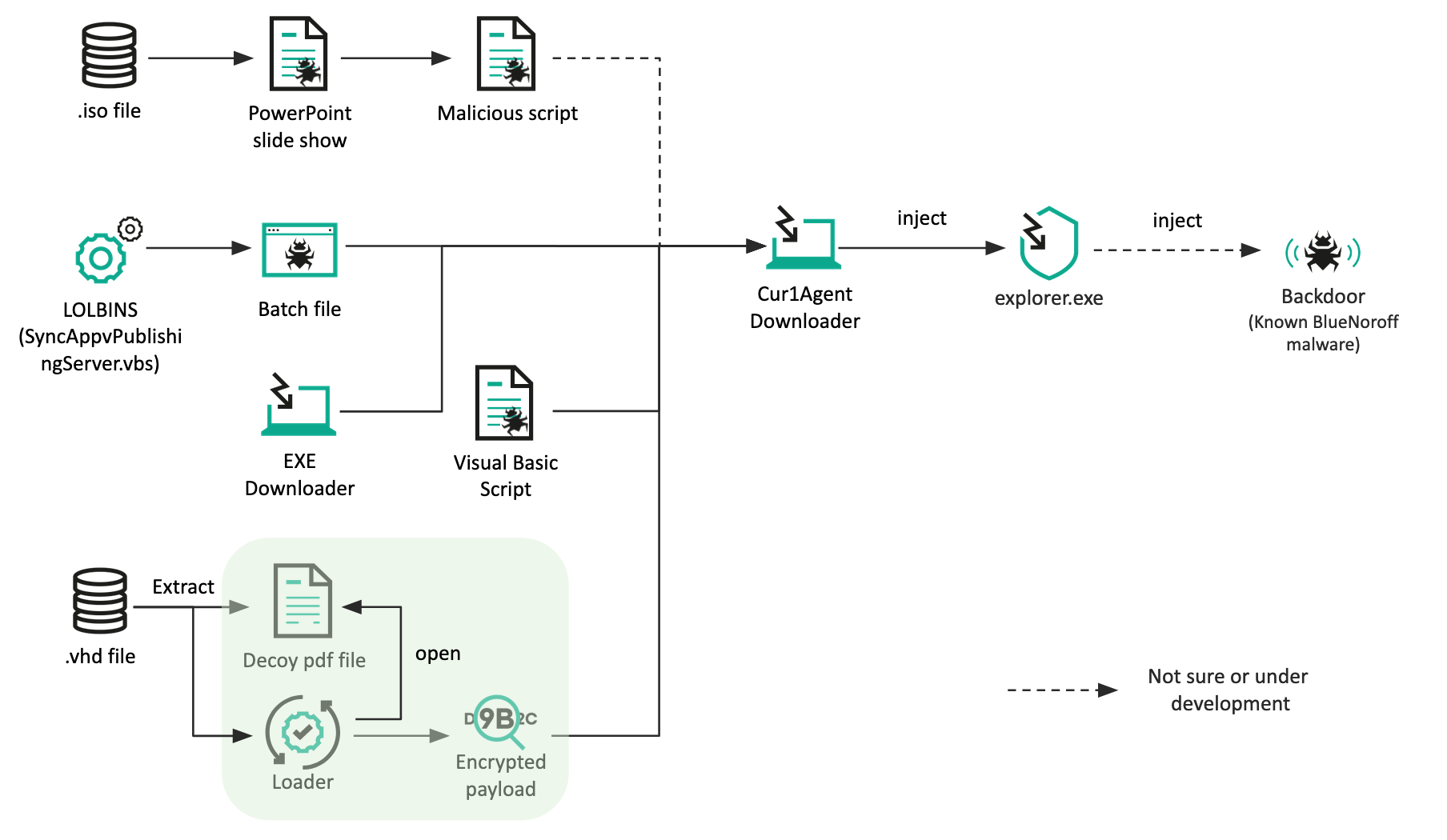
HTTP header based phishing attack detection using machine learning - Shukla - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
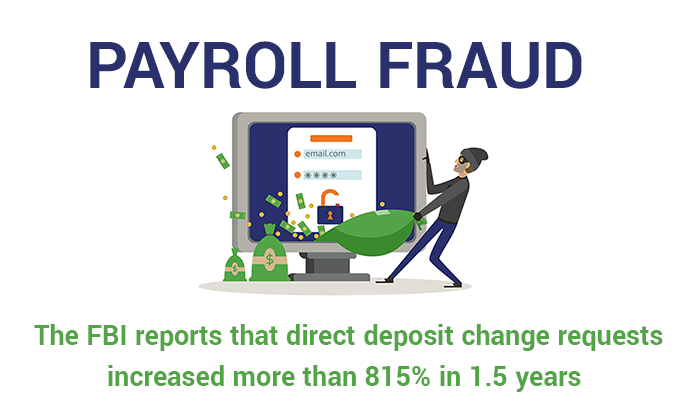
Payroll Fraud: A Growing BEC Threat to Businesses and Employees Alike - Hashed Out by The SSL Store™
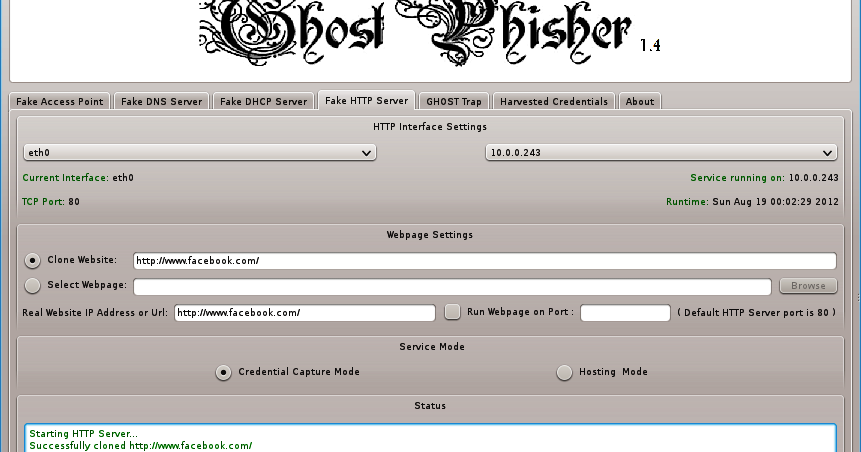

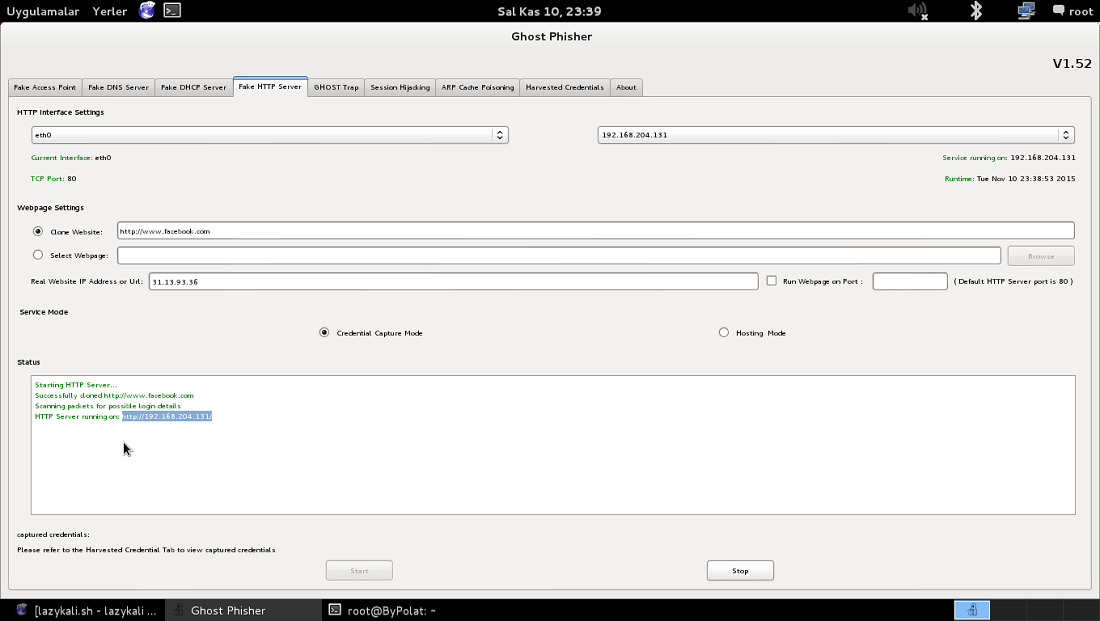




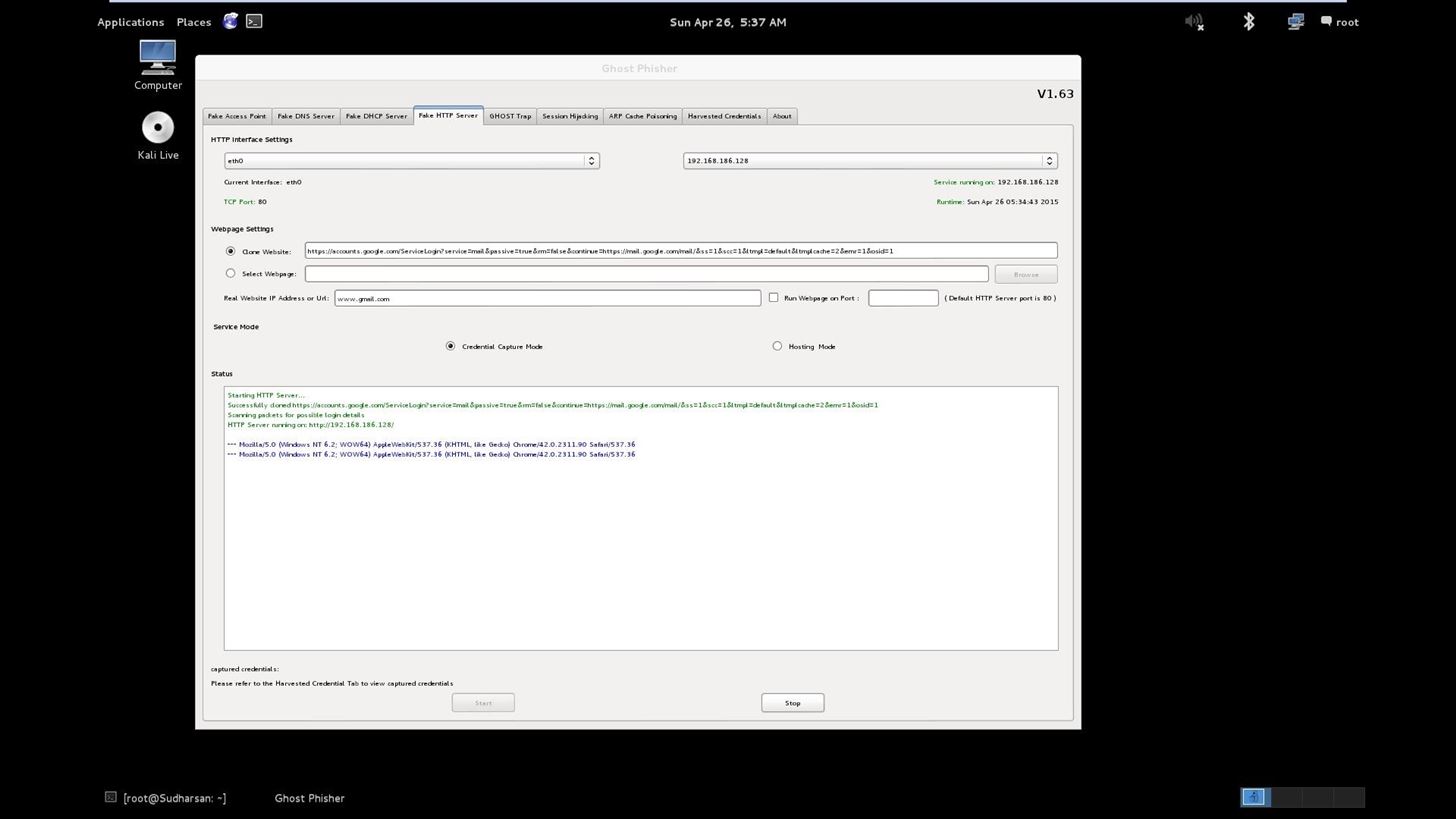
![Ghost Phisher v1.5] GUI suite for phishing and penetration attacks Ghost Phisher v1.5] GUI suite for phishing and penetration attacks](http://2.bp.blogspot.com/-9Z93jnb5M7k/UsM-961nN1I/AAAAAAAABgY/WIEhuWGVYpA/s1600/ghost_phisher.png)
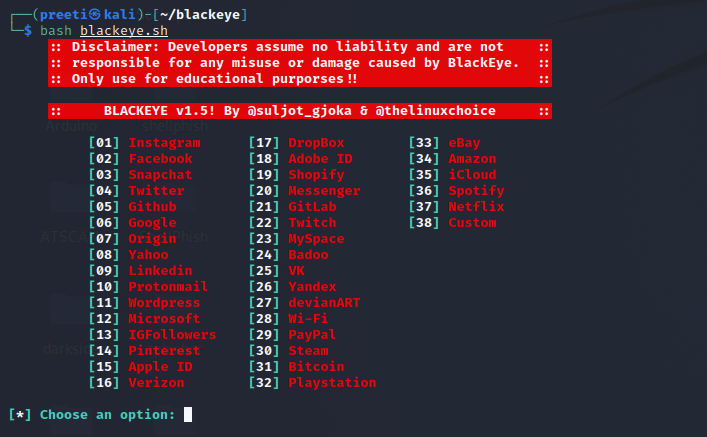
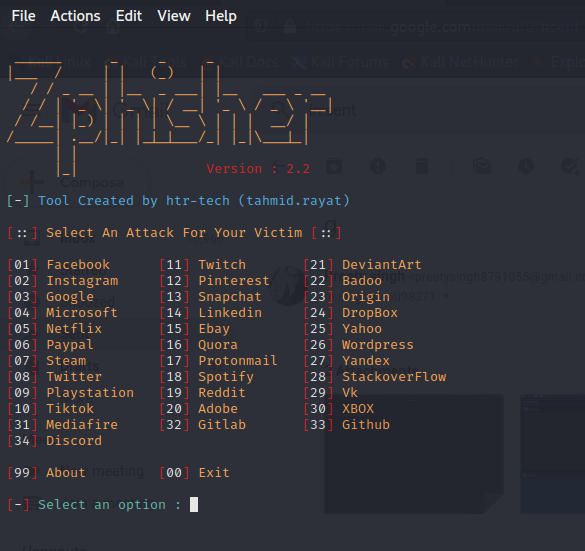
![How to do it... - Kali Linux - An Ethical Hacker's Cookbook [Book] How to do it... - Kali Linux - An Ethical Hacker's Cookbook [Book]](https://www.oreilly.com/api/v2/epubs/9781787121829/files/assets/5de7687f-5874-4b4e-b824-7421144c0eb5.png)