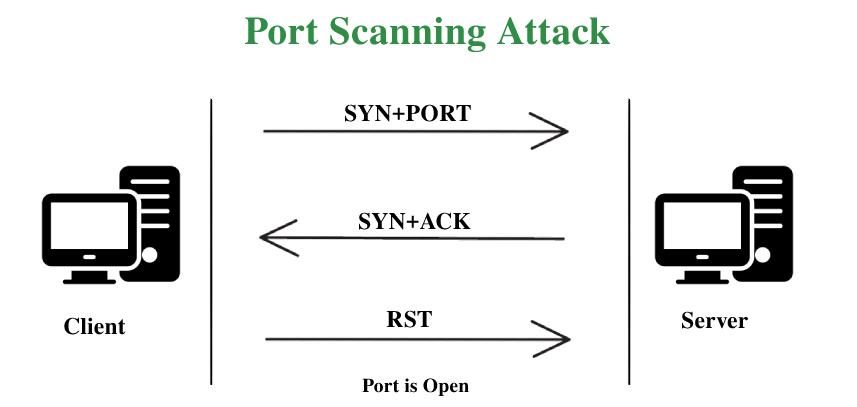
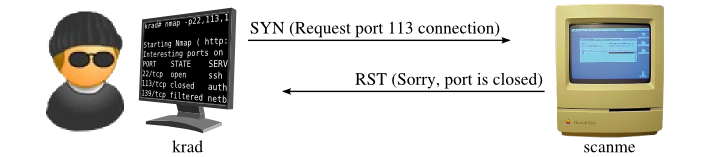
![End]Network Vulnerability and Scanning: Other NMAP Scans (NULL,FIN,XMAS,ACK,IDLE) | by Koay Yong Cett | Medium End]Network Vulnerability and Scanning: Other NMAP Scans (NULL,FIN,XMAS,ACK,IDLE) | by Koay Yong Cett | Medium](https://miro.medium.com/v2/resize:fit:1400/1*I1QeddIucKOHIGaItPl-Qw.png)
End]Network Vulnerability and Scanning: Other NMAP Scans (NULL,FIN,XMAS,ACK,IDLE) | by Koay Yong Cett | Medium

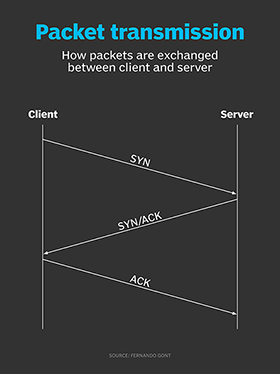
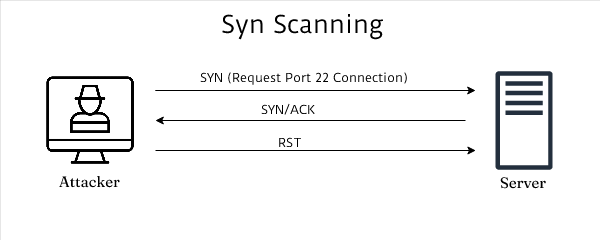
NMAP – How to run an NMAP -sS SYN Stealth Scan on Windows 7 – The Visual Guide | University of South Wales: Cyber University of the year: Three years running: 2019, 2020, 2021

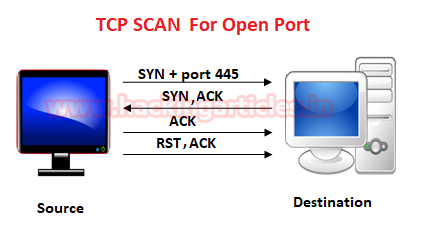
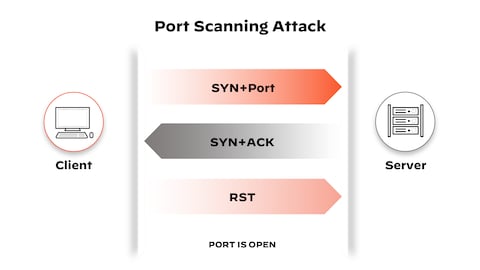
Stealth Port Scan However, if there is a service listening on the port,... | Download Scientific Diagram

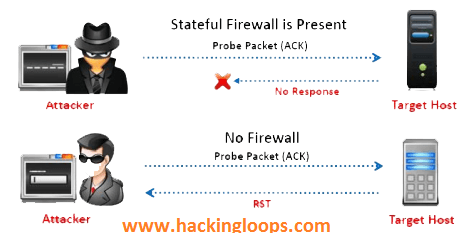
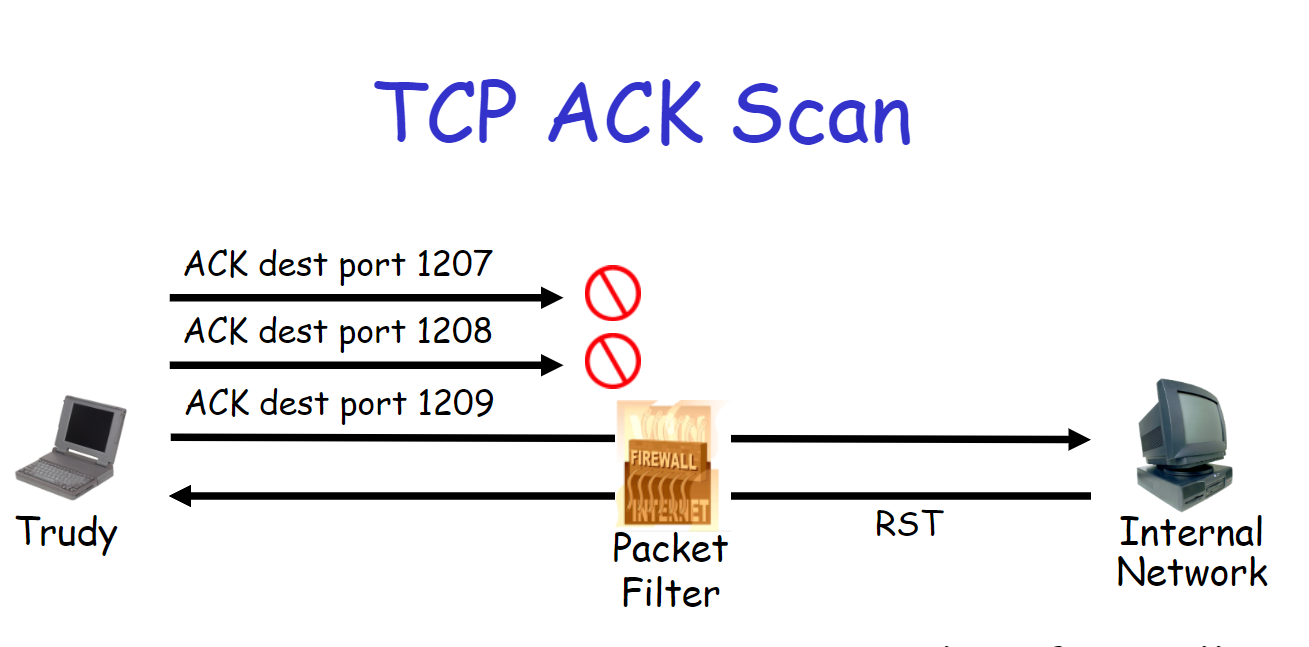
DOS Attack Ack Scan: What To Do When Your Router Logs It & How To Prevent One In The Future - One Computer Guy